Cyber threats are growing in scale and complexity in today's interconnected world. The risks are even more significant for small and mid-sized organizations with limited cyber security resources.
Crowe MacKay's Technology Consultants provide an overview of ransomware trends in 2023, detailing the threats, their economic impact, and the strategies you can employ to protect your organization. If you want to develop a cyber security strategy that helps protect your business against cyberattacks and data breaches, contact our experts in Alberta, British Columbia, Northwest Territories, or the Yukon.
Ransomware Trends 2023: Still Going Strong
2023 has shown that ransomware remains an attack of choice for malicious actors. Organizations are being targeted directly or in blanketed attacks targeted at their specific industry. The human element remains the most successfully targeted vector for launching ransomware attacks against organizations.
Understanding the Threat Landscape
Evolution of Ransomware
Ransomware has come a long way from the primitive "lockers" of 10-15 years ago that would merely freeze your screen or present a message. Today's ransomware uses sophisticated encryption algorithms to lock companies out of their data and to hold sensitive information hostage. In most cases, decryption is impossible without the key, and attackers may no longer just be looking for a monetary ransom from their victims to restore their data. The malicious software is packaged and sold readily on the dark web and easily adjusted or modified to target a specific organization. Ransomware has become a low-effort, high-reward, broad-reaching attack.
Emerging Tactics
Ransomware is no longer just about encrypting your files and demanding payment. Attackers are also exfiltrating data that they have locked. The exfiltrated data can be mined for valuable items like personal information, login credentials, or threatened to be leaked publicly if the ransom is not paid.
According to the 2023 Verizon Data Breach Investigations report, ransomware was utilized in close to 80% of system intrusions.
Email is one of the most common ransomware entry points into an organization's systems. Stolen credentials, software vulnerabilities, and unpatched zero-day exploits are commonly used to gain a foothold and deploy ransomware. End users may be the perfect target for ransomware if they do not have sufficient security training, unpatched vulnerabilities, or if multiple forms of authentication are not being used in an organization's systems.
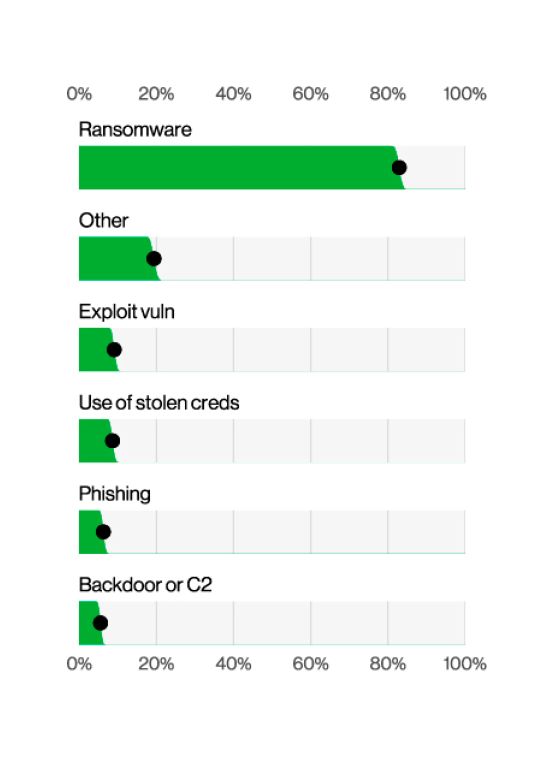
2023 Verizon Data Breach Investigations Report
The Economic Impact
The economic ramifications of ransomware attacks extend beyond the immediate ransom payment. We do not typically recommend that an organization pay the cyber criminals the demanded ransom.
Apart from the immediate demanded cost by the attacker, organizations must consider the expenses related to system downtime, data recovery, and reputational damage. Organizations could face lawsuits and regulatory fines if sensitive employee or customer data is compromised during an attack.
The IBM Security – Cost of a Data Breach Report lists the average cost of a data breach at $4.45M USD in 2023.
Best Practices for Prevention
A proactive approach is always better than a reactive one regarding ransomware.
Multi-layer Security Measures
A comprehensive cyber security strategy involves multiple layers of protection. This includes but is not limited to, firewalls, antivirus software, data backups, and multi-factor authentication.
Regular Updates and Patches
Ensure your systems are updated with the latest patches and your security software definitions are current. Outdated systems are low-hanging fruit for cybercriminals.
Employee training
Most ransomware attacks involve a human element in their execution. It is imperative that an organization's staff, contractors, and management undergo regular security awareness training and testing.
Recovering from a Ransomware Attack
If you fall victim to ransomware, all isn't lost!
Response Plan
Have a well-defined incident response plan that outlines the steps from identifying the attack, mitigating the attack, and to notifying the relevant stakeholders and authorities. Make sure this plan is accessible even if you have been subjected to a ransomware attack.
Insider threats are also a real possibility; be sure to identify and mitigate risks from within before they happen.
When All Else Fails
Sometimes, last-resort measures like isolating infected systems and utilizing offline backups could save your organization from total devastation.
FAQs: Quick Answers to Pressing Concerns
What's the Average Ransom Payment in 2023?
The average ransom has escalated and is now almost double what was seen in 2022. The Sophos State of Ransomware 2023 report puts the average ransom at $1.54M USD. Paying a ransom does not guarantee the safe return of your data!
Are Mid-Sized Businesses More Vulnerable?
Absolutely, because mid-sized businesses often lack the robust cyber security infrastructure that large enterprises can afford.
How Do I Report a Ransomware Attack?
Firstly, inform local law enforcement agencies. Canadian organizations and individuals can report cyber incidents through the Canadian Centre for Cyber Security.
How Long Does It Take to Recover?
Recovery timelines vary greatly, but expect at least one to four weeks, depending on the complexity of the attack and your preparedness level.
What Are Common Attack Vectors?
Phishing emails remain the most common delivery method. Other vectors include exploiting unpatched software and utilizing stolen or compromised credentials.
Is Cyber Insurance Worth It?
While it's an added cost, cyber insurance can be a financial lifesaver. However, scrutinize the policy to understand what exactly is covered. You may also want to undertake a cyber security assessment to determine what you need to qualify for insurance coverage.
The Best Offense is a Good Defense
Awareness is the first step in the battle against ransomware, but action is the key. An excellent defensive starting point is creating a cyber security strategy. Contact Crowe MacKay's Technology Consultants; they can assist you in developing and implementing a strategy that helps protect your business against cyberattacks and data breaches.
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.

