The cyber regulatory landscape in Europe went through a major shift after both the Directive on Measures for a High Common Level of Cybersecurity across the Union ('NIS2') and the Critical Entities Resilience Directive ('CER') entered into force in 2023. Accordingly, Member States need to transpose both directives into national law by 17 October 2024, while the measures will start applying the following day.
Given this upcoming deadline, scoped organisations are now tasked to realign and further invest in their compliance efforts, as these regulatory developments impose more stringent accountability and transparency reporting requirements.
Breaches are becoming more costly. According to PwC's 2024 Global Digital Trust Insights survey, 36% of the respondents have faced $1M+ data breaches last year.
Who will be affected by NIS2?
The NIS2 substantially broadens the scope of the original NIS Directive, which previously applied only to 'Operators of Essential Services' and 'Digital Service Providers'. Going forward, the NIS2 will apply to a larger pool of service providers as long as they qualify as 'essential' and 'important' entities under the directive.
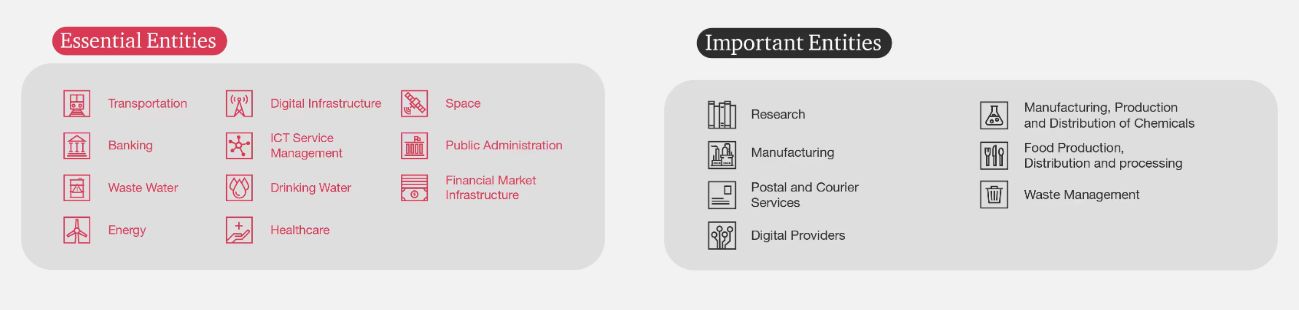
However, not all organisations which operate under the defined sectors are going to fall within scope of the NIS2: business owners will also need to look at the location of their activities and the size of their business (as defined in terms of European law). Carrying out a scoping exercise early on to map the potential impact of the provisions, is certainly recommended.
Regardless of their classification, all scoped entities will be subject to the same set of obligations (including rules on incident response and reporting, supply chain risk management, and business continuity), and both categories of entities will be subject to GDPR-style fines:
- Essential entities:Up to €10 million or 2% of the worldwide annual turnover; and
- Important entities:Up to €7 million or 1.4% of the worldwide annual turnover.
Importantly, management bodies of essential and important entities can also be held liable for breach of their organisation's obligations.
What about the CER?
The CER aims to strengthen critical infrastructures against physical threats such as natural hazards, terrorist crimes, or sabotage. Similar to the NIS2, the CER sets forth specific sectors (11 in total) which are deemed 'critical' and which fall within its scope. These include providers of transport, banking, food, and health services.
Scoped entities must, inter alia, carry out a risk assessment to identify the risks that may disrupt their services, ensure adequate physical protection of their premises and critical infrastructure, respond to and mitigate incidents, and ensure adequate employee security management and awareness.
Business executives understand that regulatory compliance provide a safety net to explore, innovate and invest.
Overlapping of NIS2 and CER
The provisions of the NIS2 explicitly provide that the directive applies to entities identified as 'critical entities' under the CER and moreover, that such critical entities will be deemed as 'essential' under the NIS2. In this respect, various organisations should be falling within the scope of both the NIS2 and the CER, making their compliance exercise more challenging.
Next Steps
The NIS2 and CER require significant efforts from concerned businesses to ensure compliance. As the cut-off date approaches, business leaders need to clarify their position under the two directives. In order to get started, the following steps may be considered:
Similar to the GDPR's record of processing activities, documenting your organisation's critical service lines, processes and assets to fully understand where you stand in terms of potential regulatory risk.
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.




