On November 10, 2020, the European Data Protection Board issued two new pieces of guidance. Read together, they outline a detailed methodology to follow when conducting data transfers under the EU General Data Protection Regulation - such guidance has been keenly anticipated following the Court of Justice for the European Union's ruling in the case commonly known as Schrems II.
The two pieces of guidance are:
- New "recommendations on measures that supplement transfer tools to ensure compliance with the EU level of protection of personal data"
- Updated "recommendations on the European Essential Guarantees for surveillance measures"
How can Cooley help you apply this methodology to your operations?
As you will see from the below - the EDPB's methodology is not uncomplicated and stresses the need for a rational and objective assessment of law and practice in importers' territories. This could require a lot of specific analysis and research.
For this reason, we have developed Cooley Transfer, an automated program that can be used by the Cooley c/d/p team to help our clients navigate the complexities of EDPB's transfer methodology. For more information on Cooley Transfer, see below.
The EDPB's methodology
The EDPB's suggested methodology is broken down into six steps:
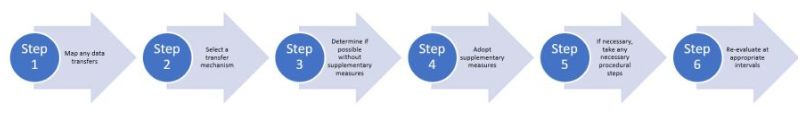
Step 1: Data transfer mapping
Exporters must:
- Map out all data transfers to non-EEA countries (including any "onwards transfers" by importers)
- Verify and document that any personal data transferred is limited to that which is adequate, relevant and necessary in the circumstances
Step 2: Select a transfer mechanism
Exporters must then select a transfer mechanism from the available options under the GDPR - namely:
- Adequacy decision - if reliance on an adequacy decision applicable to the importer is the legal basis being relied on for a transfer, no further steps outlined below need to be taken.
- Appropriate safeguards (aka transfer tools) -
- If use of a transfer tool to establish appropriate safeguards is the legal basis being relied on for a transfer, the further steps below must be followed - starting with Step 3.
- The principal transfer tools that may be used to establish
appropriate safeguards for a transfer are:
- Standard Contractual Clauses - an updated form of which was released for public consultation by the European Commission on November 12. Keep an eye out for an upcoming post in which we will analyze these updated SCCs.
- Binding Corporate Rules
- Codes of Conduct
- Certification Mechanisms
- Ad Hoc Contractual Clauses
- Derogation -
- If reliance on a derogation is the legal basis being relied on for a transfer, no further steps outlined below need to be taken.
- However, consistent with its previous guidance, the EDPB is at pains to remind organizations that these derogations "must be interpreted restrictively and mainly relate to processing activities that are occasional and nonrepetitive" - i.e., they are unlikely to be much use in the context of transfers carried out as part of the day-to-day business operations of most organizations.
Step 3: Determine whether your selected transfer tool works without supplementary measures
Exporters using a transfer tool must assess whether there is any law or practice in the importer's territory that would render the selected transfer tool ineffective for its required purpose (i.e., by undermining the level of protection that the tool in question is designed to establish).
What should this assessment involve?
This assessment should:
- Consider applicable laws in the importer's territory that are relevant to the transfer in question (i.e., consider the nature of the data transferred, the nature of the importer and the laws relevant to that data and that importer).
- Focus particularly on laws in the importer's country relating to public authorities' rights to access the transferred data and/or to compel the importer to disclose the transferred data (e.g., for purposes of criminal law enforcement, regulatory supervision and/or national security).
- In the absence of codified and available legislation
controlling public authorities' rights to compel disclosure of
transferred data and/or to access transferred data -
- Factor in an objective assessment of the wider background relating to those matters in the importer's country (e.g., reported precedents, legal powers, and the technical, financial and human resources at relevant authorities' disposal, etc.).
- Not rely on subjective factors such as the likelihood of public authorities' access to transferred data.
What is the relevant standard to apply?
When assessing public authorities' powers to compel disclosure of and/or to access transferred data, the EDPB states that the key question to ask is: are those powers limited to what is necessary and proportionate in a democratic society?
To answer the question of what is "necessary and proportionate in a democratic society" in this context - the EDPB notes that four essential guarantees must be present:
- Processing should be based on clear, precise and accessible rules
- Necessity and proportionality with regard to the legitimate objectives pursued need to be demonstrated
- An independent oversight mechanism should exist
- Effective remedies need to be available to the individual
What next if it is determined that the powers are limited to what is necessary and proportionate?
If this is the case - the powers do not necessarily render the selected transfer tool ineffective for the required purpose, and no further steps below need to be followed.
What next if it is determined that the powers are NOT limited to what is necessary and proportionate?
If this is the case -
- The powers are likely excessive, and likely to undermine the level of protection that the transfer tool in question is designed to create.
- Those powers are likely to render the selected transfer tool ineffective for the required purpose without further additional protections being applied.
- Therefore, supplementary measures are required - see Step 4.
What does the EDPB say about 702 FISA - does that go beyond what is necessary and proportionate?
The EDPB makes express reference to the fact that the CJEU found in Schrems II that Section 702 of the US Foreign Intelligence Surveillance Act (702 FISA) "does not respect the minimum safeguards resulting from the principle of proportionality under EU law and cannot be regarded as limited to what is strictly necessary".
Accordingly, if an importer or recipient of an onwards transfer falls under 702 FISA - the relevant transfer tool being used will need supplementary measures to be effective (again, see Step 4 below - particularly What does all this ultimately mean where a transfer involves an organization who falls under 702 FISA?).
Step 4: Adopt supplementary measures
Where necessary, exporters should then identify and adopt supplementary measures to bring the level of protection of the transferred data up to the required standard.
What types of supplementary measures are available?
Three types of supplementary measures are suggested by the EDPB:
- Technical measures - for example, only providing the transferred data to the exporter in pseudonymized form and keeping the key enabling reidentification in the EEA.
- Contractual measures - for example, introducing an obligation on the importer to notify data subjects of a relevant request or order received from a public authority.
- Organizational measures - for example, regular publication of transparency reports or summaries regarding requests from public authorities for access to data and the nature of any reply(ies) provided.
Are any supplementary measures better than others?
In certain circumstances: yes.
The EDPB stresses that in the context of laws relating to surveillance and access to data (such as 702 FISA) - contractual measures and organizational measures alone will not suffice.
Only robust supplementary technical measures (such as pseudonymization or encryption pre-transfer) are likely to be sufficient to reasonably impede or render ineffective access by public authorities to the transferred data.
Does this mean supplementary technical measures are always required for transfers involving organizations subject to 702 FISA?
The EDPB expressly provides that if an importer or recipient of an onwards transfer falls under 702 FISA - additional technical measures need to be deployed to make access by US authorities to the transferred data "impossible or ineffective" (e.g., pseudonymization or encryption of data pre-transfer - and retention of the relevant key in the EEA or otherwise outside the scope of US authorities' jurisdiction).
What if no supplementary measures will suffice?
In those cases where no combination of supplementary measures will be sufficient to create the necessary standard of protection for the transferred data - exporters must avoid, suspend or terminate the transfer.
What does all this ultimately mean where a transfer involves an organization who falls under 702 FISA?
The positions noted above - when read in combination - appear to mean that organizations exporting personal data to organizations who fall under 702 FISA should either:
- ensure they adopt adequate technical measures; or
- must find comfort in the technical measures that are being implemented by the relevant importing organizations.
If neither can be done, the exporting organization should avoid, suspend or terminate such data transfers.
It remains to be seen how eager data protection authorities will be in challenging the technical measures that are being implemented in this context, as this requires an in-depth analysis of the effectiveness of information security measures.
Step 5: If necessary, take any required procedural steps
Where relevant, exporters should then take any formal procedural steps to give effect to the transfer tool in question (as strengthened with the relevant supplementary measures).
For example: seeking an authorization from a supervisory authority to rely on ad hoc contractual clauses as a transfer tool - this would include reliance on amended-form SCCs that contradict or are inconsistent with the approved-form SCCs (which may, theoretically, occur as a result of the introduction of certain supplementary measures noted above - although we believe this will be unlikely in most cases).
Step 6: Reevaluate at appropriate intervals
Finally - exporters, working with importers, should reevaluate at appropriate intervals the level of protection afforded to the transferred data. This reevaluation should include regular monitoring of relevant developments that may affect the protection afforded to transferred data (e.g., updates to laws or changes in practice in the importer's country) and may lead to adapting the transfer tool or reconsidering the data transfer itself.
Using Cooley Transfer to apply the EDPB's methodology to your organization
As noted above, we have recently developed Cooley Transfer - an automated tool that helps us apply the EDPB's transfer methodology to our clients' various data transfer scenarios on a consistent, scalable and objective basis. Its core functionality includes:
- Mapping clients' data transfers - i.e., documenting importers, the nature of the transferred data, the transfer mechanisms being relied upon, etc.
- Auto-generating compliance assessments for each given transfer scenario - these assessments will be produced by automatically applying an analysis of relevant law and practice in each given importing organization's territory.
- Where necessary, suggesting such technical, contractual and/or organizational supplementary measures as may be required to seek to ensure that relevant transfers comply with the GDPR.
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.


